
Monitoring Network Traffic
on Mobile Devices
What information is your phone sending out? And to whom?
2021-2022 Comprehensive Exercise Computer Science Department
3rd-Party Apps
Wireshark
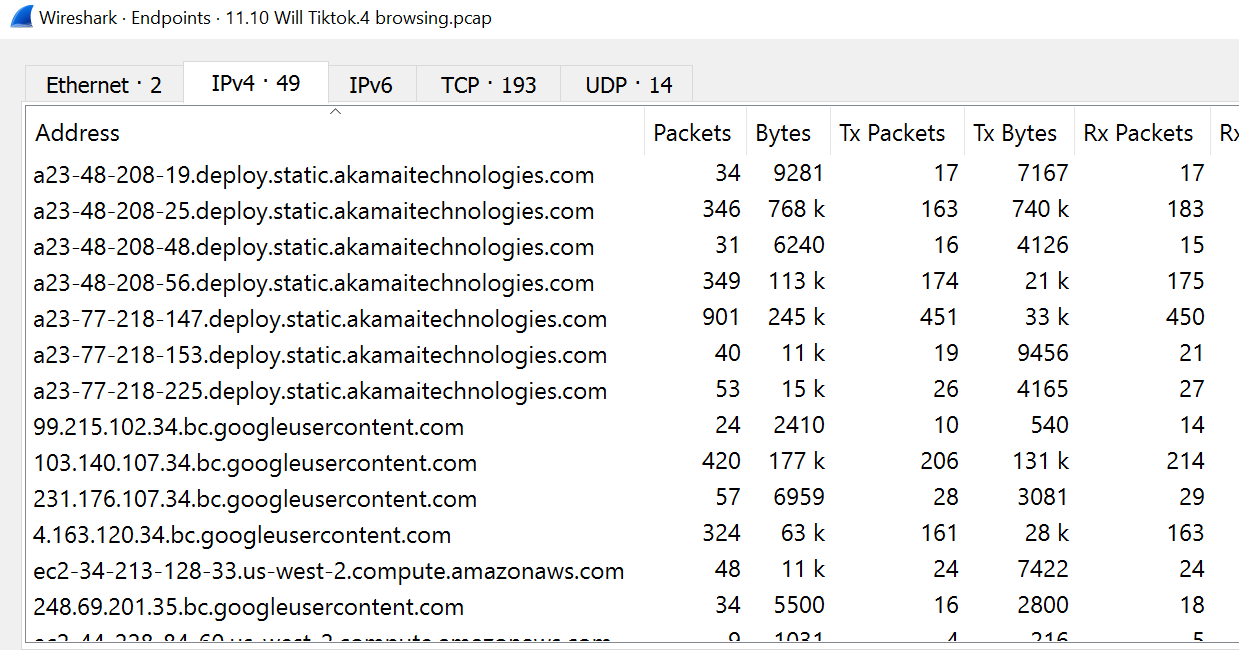
This tool, which we used for much of our analysis and data collecting, is free and open source. On iOS, traffic was monitored through a virtual interface created by Wireshark and saved in a .pcap, or "packet capture" file. With these files, we can use Wireshark to view all of the packets incoming and outgoing through a specific capturing session.
Wireshark can also get us information on the addresses from which data is being received or sent to, as well as the size of the packets in bytes. It has many other features, including port filtering and conversion to .csv, which is how we later performed the majority of our data visualizations.
tPacketCapture
Available on the Google Play Store, this app is what we used to monitor traffic on Android devices. Using the built-in VPN service from Android OS, this app sets up as a "man-in-the-middle" and records information on incoming and outgoing packets, saving them in a .pcap file that we can then analyze with Wireshark.
Jupyter
We used jupyter notebook to write quickly iterable code to produce and view graphs.
It allowed for us to test hypothesis and learn about our data in an efficient manner.
Pandas
With Pandas, we analyzed the exported csv files. The package supports fast mathematical operations and works directly with MatPlotLib.
MatPlotLib
MatPlotLib enabled rapid customized visualization of our data in various formats.
About The Project
Who is
Your Phone Talking to?
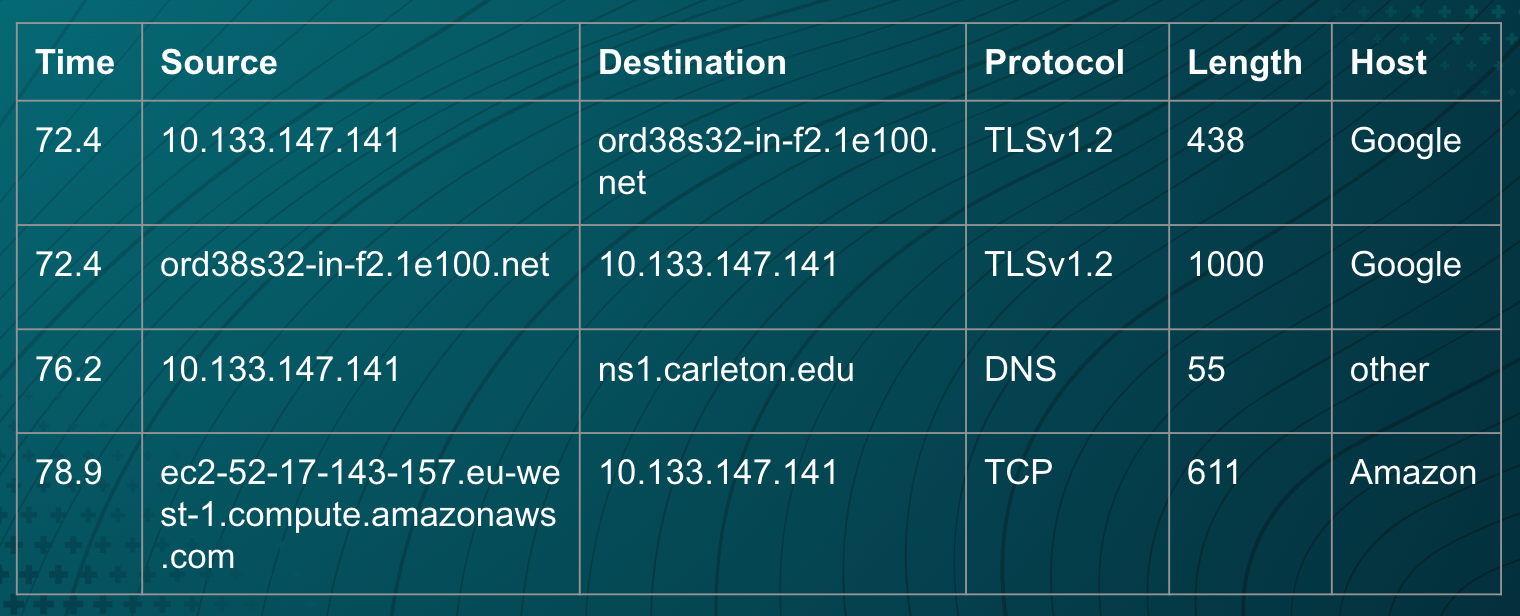
What info are our phones sending? And to whom? Using different collection methods, we monitored traffic on our phones while browsing apps like TikTok and Facebook.
Although the majority of data being sent and received is encrypted, what can we infer from the information we have, such as packet size or destination?
Meet Us

Will Gershman

Kristin Albright

Fabricio Rua-Sanchez

Rudra Subramanian

Hashir Safdar